Introduction to Malware & Monsters
The Philosophy Behind the Experience
Cybersecurity is fundamentally a collaborative discipline. Real incidents require diverse expertise, clear communication, and coordinated response. Yet most cybersecurity training isolates learners in individual exercises or passive presentations.
Malware & Monsters flips this approach through our innovative security training platform. Instead of learning about cybersecurity, you practice cybersecurity education through realistic, team-based security training scenarios. Our gamified incident response training transforms traditional learning into engaging incident response simulation experiences that build real cybersecurity skills.
Learning Through Discovery
In every Malware & Monsters session that focuses on collaborative learning cybersecurity:
- Your knowledge drives the content. The Incident Master facilitates, but your expertise and insights create the learning experience.
- Questions matter more than answers. The goal isn’t to memorize facts, but to develop the thinking skills that drive cybersecurity skills development.
- Mistakes become insights. When approaches don’t work, the team learns together why and develops better strategies.
- Collaboration creates confidence. Working with teammates builds both technical skills and communication abilities essential for security professional development.
How Sessions Work
The Basic Structure
Every Malware & Monsters session follows a three-phase incident response structure:
Discovery Phase (Round 1): Your team investigates initial symptoms to identify what type of threat you’re facing. Each team member approaches the investigation from their role’s perspective, then shares findings to collectively identify the specific Malmon.
Investigation Phase (Round 2): With the threat identified, your team analyzes the scope of the incident, understands the attack progression, and assesses potential impact. This phase often reveals the Malmon’s attempts to evolve or escalate.
Response Phase (Round 3): Your team coordinates a comprehensive response strategy, implements containment measures, and works to neutralize the threat before it can cause maximum damage.
Your Role in the Team
Rather than playing a generic “cybersecurity professional,” you’ll take on a specific role that matches your interests and expertise:
- Detective: You excel at finding clues and analyzing evidence
- Protector: You focus on stopping threats and securing systems
- Tracker: You monitor data flows and network behavior
- Communicator: You handle stakeholder relations and coordinate response
- Crisis Manager: You oversee the overall incident response strategy
- Threat Hunter: You proactively search for hidden threats and attack indicators
These roles aren’t rigid job descriptions - they’re lenses through which you approach problems, ensuring every team member contributes their unique perspective.
What Makes Malmons Special
Digital Threats as Creatures
In Malware & Monsters, malware families are represented as Malmons - digital creatures with distinct personalities, capabilities, and behaviors. This isn’t just a creative choice; it reflects how cybersecurity professionals actually think about threats.
Just as biologists classify animals by species with predictable behaviors, cybersecurity professionals categorize malware families by their attack patterns, evasion techniques, and objectives. A GaboonGrabber behaves differently from WannaCry, which behaves differently from Stuxnet.
Legacy and Contemporary Threats
Your Malmon encounters span cybersecurity history, helping you understand how threats evolved:
Legacy Malmons represent foundational attacks that shaped the field - Code Red (2001) demonstrated internet-scale worm propagation, Stuxnet (2010) revealed nation-state capabilities, and Gh0st RAT (2008) pioneered APT techniques still used today.
Contemporary Malmons reflect current threat landscapes - LockBit represents modern ransomware operations, FakeBat shows today’s loader tactics, and WannaCry bridges legacy vulnerabilities with contemporary impact.
This historical perspective helps teams recognize patterns, understand why certain defenses exist, and apply lessons from past incidents to current challenges.
The Type System
Every Malmon belongs to one or more types that determine its strengths and weaknesses:
- Trojan-types excel at deception but struggle against behavioral analysis
- Worm-types spread rapidly through networks but can be contained through isolation
- Ransomware-types threaten data integrity but are vulnerable to backup strategies
- Rootkit-types hide deep in systems but can be exposed through forensic techniques
Understanding these type relationships helps you choose the most effective response strategies.
Evolution and Adaptation
Malmons can evolve during incidents, gaining new capabilities and becoming more dangerous. A basic Trojan might evolve into an Advanced Persistent Threat if not contained quickly. This evolution mechanic reflects how real cyber attacks escalate when not addressed promptly.
Example Malmon Card
Here’s what a typical Malmon card looks like:
GaboonGrabber
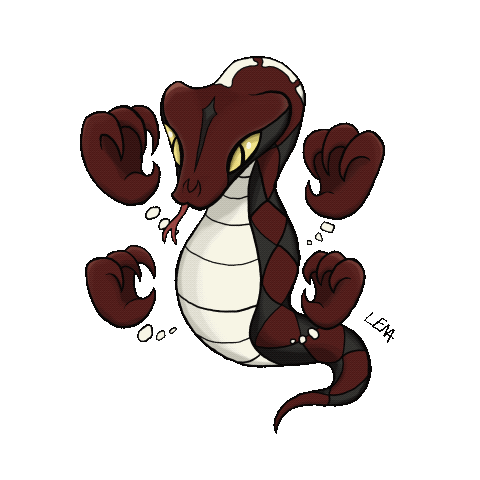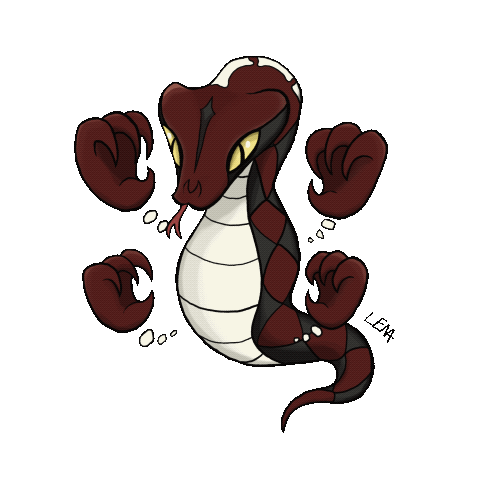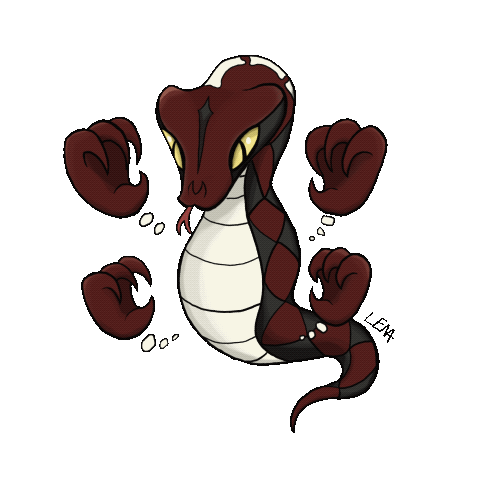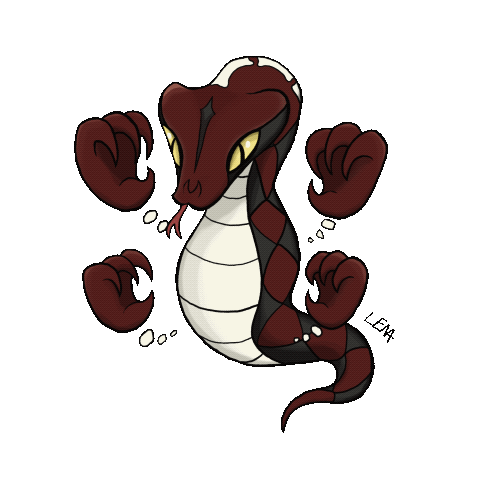
GaboonGrabber was discovered and named by Lena aka LambdaMamba, and is the first Malmon ever created. Written in .NET, it extracts embedded resources to launch multiple fileless stages. It camouflages itself as legitimate software—even mimicking app code—to avoid detection. Its final stage can deploy threats like Snake Keylogger, AgentTesla, Redline, Lokibot, and more.
Each Malmon card provides essential information for understanding the threat’s behavior, capabilities, and vulnerabilities - helping your team choose the most effective response strategies.
The Learning Experience
Building Real Skills
While the creature-collection framework makes learning engaging, every mechanic teaches genuine cybersecurity concepts. Research demonstrates that game-based learning environments effectively enhance skill acquisition and knowledge retention (Gee 2003; Connolly et al. 2012):
- Type effectiveness teaches you to match defensive strategies to specific threat categories
- Evolution mechanics demonstrate how attacks escalate when not contained quickly
- Collaborative investigation builds the communication skills essential for incident response (Johnson, Johnson, and Holubec 1999)
- Role specialization helps you understand how different security functions work together
Safe Environment for Growth
Malware & Monsters creates a safe space to develop cybersecurity expertise through social learning processes (Vygotsky 1978):
- Ask questions without feeling inexperienced
- Make mistakes and learn from them collaboratively
- Share knowledge and learn from others’ expertise
- Practice communication across different technical backgrounds
- Build confidence in your ability to contribute to security teams
Community Knowledge Building
Every session contributes to a growing collection of community knowledge:
- MalDex entries document your team’s encounters with different Malmons
- Response strategies get shared with other teams and organizations
- Lessons learned help improve future incident response
- Technique sharing spreads effective practices across the community
What to Expect in Your First Session
Character Creation
You’ll start by sharing your cybersecurity-related experience with your teammates. This could be professional work, academic study, hobby projects, or just general curiosity about technology. Based on these interests and team needs, you’ll collaboratively choose roles.
Then you’ll develop your character - keeping your real name but building a personality around your chosen role. Are you a paranoid Detective who notices every anomaly? A protective Protector who takes attacks personally? A methodical Crisis Manager who thinks in flowcharts? Have fun with the archetypes while staying true to your actual interests.
Example Role: Detective
🎭 Archetype
💪 Strengths
• Pattern Recognition: Spotting anomalies in logs and behavior
• Evidence Analysis: Connecting clues into attack timelines
🎯 Focus Areas
• System logs and process executions
• Attack vector analysis and entry points
🎪 Roleplay Tips
• Be curious about details others might skip
• Share your thought process: 'This pattern suggests...'
During investigations, you might collect evidence artifacts - pieces of information from incident reports, system logs, or security alerts that help your team understand what happened.
The Incident Begins
Your Incident Master will present initial symptoms - computers running slowly, suspicious emails, unusual network traffic. Your team investigates these symptoms from different role perspectives, sharing discoveries and building toward identifying the specific Malmon you’re facing.
Collaborative Problem-Solving
Throughout the session, you’ll work together to understand the threat, assess its impact, and coordinate an effective response. The Incident Master facilitates this process through questions and guidance, but your team’s knowledge and decisions drive the experience.
Learning Through Reflection
Sessions conclude with reflection on what you discovered, what strategies worked, and what you might do differently. These insights get captured in your team’s MalDex entry and shared with the broader community.
Getting the Most from Your Experience
Embrace Your Role
Don’t worry about being the “smartest” person in the room. Each role brings valuable perspectives, and the best solutions emerge from diverse viewpoints working together.
Ask Questions
If you don’t understand something, ask. If you’re curious about a technique someone mentioned, explore it. If you disagree with a proposed approach, voice your concerns. Questions drive learning and often reveal important insights.
Think Like Your Character
Get into your role’s mindset. How would a Detective approach this evidence? What would worry a Protector about this attack? How would a Communicator explain this to management? Role-playing enhances both engagement and learning.
Learn from Others
Pay attention to how your teammates think through problems. What questions do they ask? What patterns do they notice? What tools do they suggest? Every session is an opportunity to expand your own mental toolkit.
Ready to Start?
Malware & Monsters sessions require no special preparation beyond curiosity and willingness to collaborate. You’ll learn the specific mechanics as you play, guided by your Incident Master and supported by your teammates.
The most important thing to remember: this is a collaborative learning experience. Your success is measured not by individual achievement, but by how well your team works together to understand and respond to cybersecurity challenges. This approach aligns with established cooperative learning principles that emphasize collective problem-solving and shared knowledge construction (Slavin 1996).
In the following chapters, you’ll learn about the specific systems and mechanics that make Malware & Monsters work - from understanding Malmon types and abilities to mastering advanced response strategies. But remember, these are tools to support collaborative learning, not rules to memorize. This experiential gaming approach builds on proven pedagogical frameworks for cybersecurity education (Kiili 2005; Cone et al. 2007).
When you arrive at your first Malware & Monsters session, you’ll need nothing more than:
- Curiosity about cybersecurity challenges
- Willingness to work as part of a team
- Openness to sharing your perspective and learning from others
- Enthusiasm for collaborative problem-solving
Everything else you’ll learn through the experience itself.